-
Notifications
You must be signed in to change notification settings - Fork 1.5k
Fix wait loop and void cast #24
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fix wait loop and void cast #24
Conversation
1.Add semaphore uninterruptible wait function 2.Replace semaphore wait loop with a single uninterruptible wait 3.Replace all sem_xxx to nxsem_xxx Change-Id: Ibde993435b011c5dda967f4445a8e791dba72aa3 Signed-off-by: Xiang Xiao <xiaoxiang@xiaomi.com>
1.Remove void cast for function because many place ignore the returned value witout cast 2.Replace void cast for variable with UNUSED macro Change-Id: Ie94ee2c34141909d06a192e6bf6104e5696bef41 Signed-off-by: Xiang Xiao <xiaoxiang@xiaomi.com>
* Simplify EINTR/ECANCEL error handling 1. Add semaphore uninterruptible wait function 2 .Replace semaphore wait loop with a single uninterruptible wait 3. Replace all sem_xxx to nxsem_xxx * Unify the void cast usage 1. Remove void cast for function because many place ignore the returned value witout cast 2. Replace void cast for variable with UNUSED macro
|
Removing the (void) cast actually violates the coding standard. Look at: http://nuttx.org/Documentation/NuttXCCodingStandard.html#retvalues Checking Return Values. Callers of internal OS functions should always check return values for an error. At a minimum, a debug statement should indicate that an error has occurred. The calling logic intentionally ignores the returned value, then the function return value should be explicitly cast to (void) to indicate that the return value is intentionally ignored. An exception of for standard functions for which people have historically ignored the returned values, such as printf() or close. All calls to malloc or realloc must be checked for failures to allocate memory. |
* Simplify EINTR/ECANCEL error handling 1. Add semaphore uninterruptible wait function 2 .Replace semaphore wait loop with a single uninterruptible wait 3. Replace all sem_xxx to nxsem_xxx * Unify the void cast usage 1. Remove void cast for function because many place ignore the returned value witout cast 2. Replace void cast for variable with UNUSED macro
|
This PR completely breaks usrsock networking for one of our projects. Underlying cause is not clear but creating a revert for commit 6a3c2ad fixed it. I suggest reverting this in any case as merging insanely big PRs like this that confuse several unrelated concepts into single commit make root cause analysis extra hard. |
|
@juniskane could you point out which patch break your networking? or which socket function break? |
|
Please help me identify which patch generate the regression like this: |
|
Does the error like this: |
|
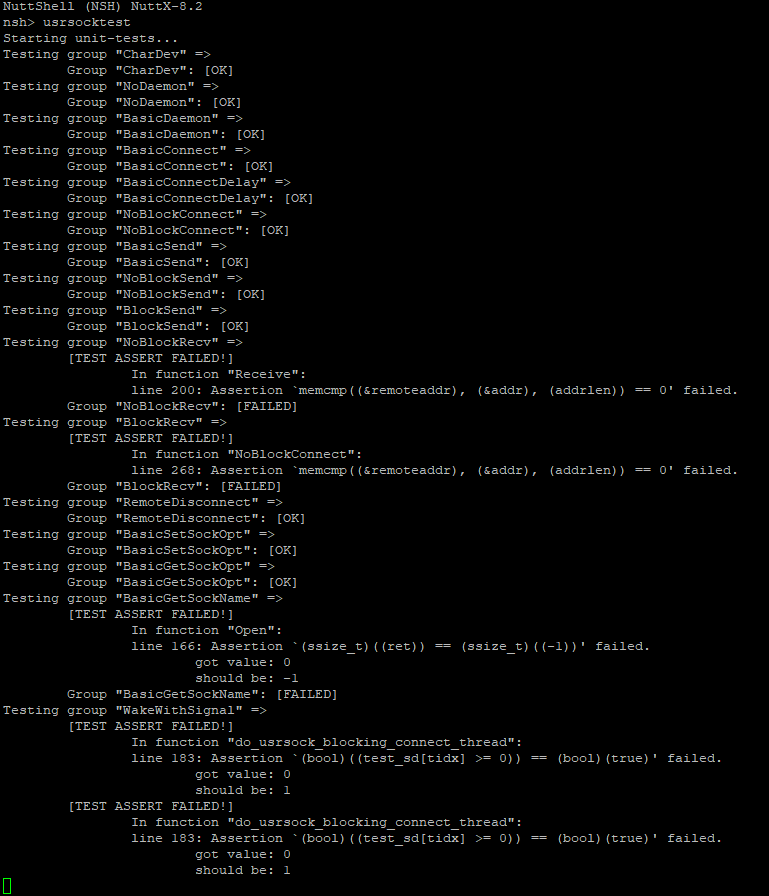
Bug appears to be reproducable with 'usrsocktest' testing application (CONFIG_EXAMPLES_USRSOCKTEST=y). The config I used for quick test is at https://gist.github.com/jkivilin/7d7558b54a85fd70c8a439d6d8feba5e With offending commit reverted, I get output: There is some other issue that causes test-cases to fail, but when 6a3c2ad is not reverted, the output changes. Now I get different errors, first being at 'Testing group "BasicSend"': Maybe above can be used to locate the issue? |
|
With 6a3c2ad reverted and https://github.com/apache/incubator-nuttx/commit/a5aac1fd5515e2447785025da4102c5b04fc6389.patch applied, usrsocktest output is the same (so problem is not with in a5aac1f): |
|
Ok, let me repro on simulator with your config |
|
I agree with Jussi, problem is caused by a9ff3e1, not the other commit. I cannot spot the problem by code reading unfortunately. This is usrsocktest with old upstream merge from December (some of the SHAs here are from our internal repository) running on proprietary STM32L4 board. Something is broken, but not as much as with a9ff3e1: usrsocktest_Dec16_master_9e3bf44870.txt Broken master: usrsocktest_Jan08_devel_5ff90c1aa27.txt Broken master + this PR reverted (identical with Dec 16 output): usrsocktest_Jan08_devel_revert_5864cf8e038.txt Broken master + this PR reverted + add a9ff3e1 (identical with broken master) usrsocktest_Jan08_devel_revert_and_add_a9ff3e1778d950f7d7.txt |
|
This is unrelated, but why is priv->tx_result ignored here (different than priv->rx_result handling)? |
My intention is to remove all result check since only interrupt handler will post semaphore, the check is redundant. |
I test your config on my simulator, the result isn't stable: BasicSend can pass sometime, but will hit segmentation fault at the later time. The old release can pass BaiscSend stably, but also will hit segmentation fault. |
|
This could be it: still looking at the patch if there more instances.... |
|
Ok. So, before adding and return value from net_lockedwait was returned for |
|
There is still something wrong. After this PR and above fix I still get error when doing netcat over cellular connection. DNS is resolved correctly but there is "polling error 12" that was not there before: [EDITED: archive trace to comment history] Nevermind, fixed this by increasing CONFIG_NET_USRSOCK_NPOLLWAITERS from 1 to 2. |
Thanks for finding the tough bug, could you send the patch fix both issues? |
Good finding, it explain why sometime the test case can pass, but sometime not. |
|
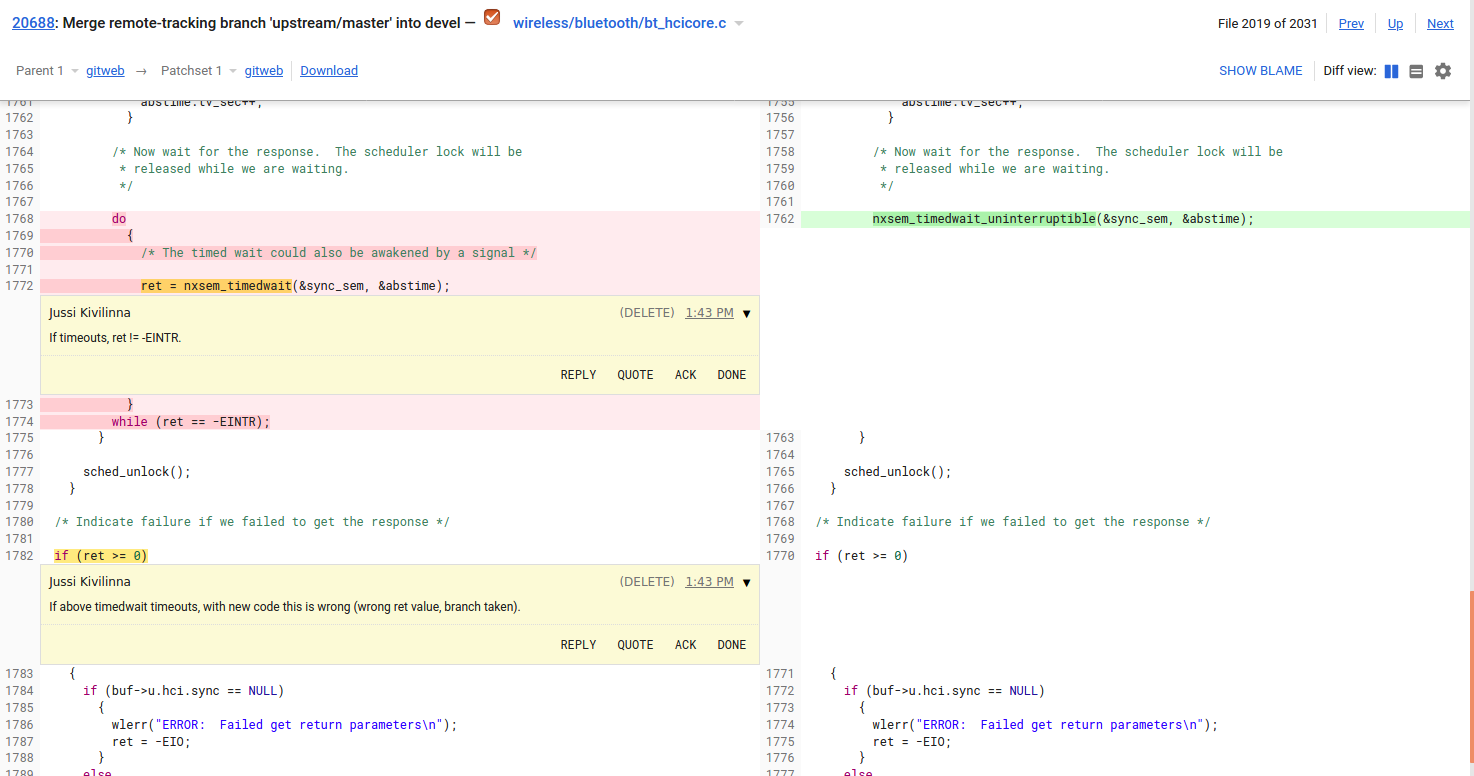
I have not reviewed CONFIG_NET_USRSOCK_NPOLLWAITERS in upstream configs. I'd expect that to be 1 most of time (only one waiting for a given socket) so no patch for that. Users of usersock have to review their projects for this value. We also found similar issues with 'ret' in: wireless/bluetooth/bt_hcicore.c Details forthcoming... |
|
Likely caused by this PR: Issue 1: In bt_hci_cmd_send_sync(): Issue 2: (also found by Jussi Kivilinna) In hcsr04_ioctl() with SNIOC_READ_RAW_DATA, uninitialized 'ret' is returned. This ioctl command also looks useless as no read data is returned to caller. Driver author @acassis to comment/fix this? No patch for these, just want to report bugs. |
|
@acassis here is the fix: |
|
Done! Thank you Xiao Xiang! |
Any reason why this bit of code is now done differently for stm32f7 and stm32f0l0g0 than for other STM32? |
I will provide a patch to bring back "do {} while (priv->XXresult == 0);". |
|
@juniskane here is the patch: |
|
Hi @xiaoxiang781216, @jkivilin! I have some problems running usrsocktest, few of them looks similar to those mentioned in this issue. I've described my issues in dev@nuttx.apache.org mailing list - topic: "Usrsocktest app example fails" |
As I remember there are two test case fail even after this fix, I will look at these two fail today or tomorrow. |
|
@lukegluke , @masayuki2009 create a fix here, please try it: |
Thanks, it fix fails in NoBlockRecv and BlockRecv indeed, but there are more complicated errors that (as I think) involve net stack. |
…ssage_by_application_api xtensa/esp32: Fix ISR send message to queue by application API
* Simplify EINTR/ECANCEL error handling 1. Add semaphore uninterruptible wait function 2 .Replace semaphore wait loop with a single uninterruptible wait 3. Replace all sem_xxx to nxsem_xxx * Unify the void cast usage 1. Remove void cast for function because many place ignore the returned value witout cast 2. Replace void cast for variable with UNUSED macro
- recorganize spi driver Signed-off-by: Runcheng Lu <runcheng.lu@hpmicro.com>
- recorganize spi driver Signed-off-by: Runcheng Lu <runcheng.lu@hpmicro.com>
set CONFIG_PRIORITY_INHERITANCE=y
set CONFIG_SEM_PREALLOCHOLDERS=0 or CONFIG_SEM_PREALLOCHOLDERS=8
apache#24 0x4dcab71 in __assert assert/lib_assert.c:37
apache#25 0x4d6b0e9 in nxsem_destroyholder semaphore/sem_holder.c:602
apache#26 0x4d80cf7 in nxsem_destroy semaphore/sem_destroy.c:80
apache#27 0x4d80db9 in sem_destroy semaphore/sem_destroy.c:120
apache#28 0x4dcb077 in nxmutex_destroy misc/lib_mutex.c:122
apache#29 0x4dc6611 in pipecommon_freedev pipes/pipe_common.c:117
apache#30 0x4dc7fdc in pipecommon_close pipes/pipe_common.c:397
apache#31 0x4ed4f6d in file_close vfs/fs_close.c:78
apache#32 0x6a91133 in local_free local/local_conn.c:184
apache#33 0x6a92a9c in local_release local/local_release.c:129
apache#34 0x6a91d1a in local_subref local/local_conn.c:271
apache#35 0x6a75767 in local_close local/local_sockif.c:797
apache#36 0x4e978f6 in psock_close socket/net_close.c:102
apache#37 0x4eed1b9 in sock_file_close socket/socket.c:115
apache#38 0x4ed4f6d in file_close vfs/fs_close.c:78
apache#39 0x4ed1459 in nx_close_from_tcb inode/fs_files.c:754
apache#40 0x4ed1501 in nx_close inode/fs_files.c:781
apache#41 0x4ed154a in close inode/fs_files.c:819
apache#42 0x6bcb9ce in property_get kvdb/client.c:307
apache#43 0x6bcd465 in property_get_int32 kvdb/common.c:270
apache#44 0x5106c9a in tz_offset_restore app/miwear_bluetooth.c:745
apache#45 0x510893f in miwear_bluetooth_main app/miwear_bluetooth.c:1033
apache#46 0x4dcf5c8 in nxtask_startup sched/task_startup.c:70
apache#47 0x4d70873 in nxtask_start task/task_start.c:134
apache#48 0x4e04a07 in pre_start sim/sim_initialstate.c:52
Signed-off-by: ligd <liguiding1@xiaomi.com>
set CONFIG_PRIORITY_INHERITANCE=y
set CONFIG_SEM_PREALLOCHOLDERS=0 or CONFIG_SEM_PREALLOCHOLDERS=8
#24 0x4dcab71 in __assert assert/lib_assert.c:37
#25 0x4d6b0e9 in nxsem_destroyholder semaphore/sem_holder.c:602
#26 0x4d80cf7 in nxsem_destroy semaphore/sem_destroy.c:80
#27 0x4d80db9 in sem_destroy semaphore/sem_destroy.c:120
#28 0x4dcb077 in nxmutex_destroy misc/lib_mutex.c:122
#29 0x4dc6611 in pipecommon_freedev pipes/pipe_common.c:117
#30 0x4dc7fdc in pipecommon_close pipes/pipe_common.c:397
#31 0x4ed4f6d in file_close vfs/fs_close.c:78
#32 0x6a91133 in local_free local/local_conn.c:184
#33 0x6a92a9c in local_release local/local_release.c:129
#34 0x6a91d1a in local_subref local/local_conn.c:271
#35 0x6a75767 in local_close local/local_sockif.c:797
#36 0x4e978f6 in psock_close socket/net_close.c:102
#37 0x4eed1b9 in sock_file_close socket/socket.c:115
#38 0x4ed4f6d in file_close vfs/fs_close.c:78
#39 0x4ed1459 in nx_close_from_tcb inode/fs_files.c:754
#40 0x4ed1501 in nx_close inode/fs_files.c:781
#41 0x4ed154a in close inode/fs_files.c:819
#42 0x6bcb9ce in property_get kvdb/client.c:307
#43 0x6bcd465 in property_get_int32 kvdb/common.c:270
#44 0x5106c9a in tz_offset_restore app/miwear_bluetooth.c:745
#45 0x510893f in miwear_bluetooth_main app/miwear_bluetooth.c:1033
#46 0x4dcf5c8 in nxtask_startup sched/task_startup.c:70
#47 0x4d70873 in nxtask_start task/task_start.c:134
#48 0x4e04a07 in pre_start sim/sim_initialstate.c:52
Signed-off-by: ligd <liguiding1@xiaomi.com>
When enable CONFIG_STACK_CANARIES, in general, the stack check in the __gcov_fork function is: " return fork(); 18: e59f3020 ldr r3, [pc, #32] @ 40 <__gcov_fork+0x40> 1c: e5932000 ldr r2, [r3] 20: e59d3004 ldr r3, [sp, #4] 24: e0332002 eors r2, r3, r2 28: e3a03000 mov r3, #0 2c: 1a00000 bne 3c <__gcov_fork+0x3c>" r3 is obtained by taking the value of sp offset. But after opening thumb, the second comparison value in "8c6: 4a06 ldr r2, [pc, #24] @ (8e0 <__gcov_fork+0x30>) 8c8: 6811 ldr r1, [r2, #0] 8ca: 687a ldr r2, [r7, #4] 8cc: 4051 eors r1, r2" is obtained through r7. Since r7 stores the stack address at this time, which stores the address of the parent process, the stack out of bounds will occur in the child process Signed-off-by: wangmingrong1 <wangmingrong1@xiaomi.com>
When enable CONFIG_STACK_CANARIES, in general, the stack check in the __gcov_fork function is: " return fork(); 18: e59f3020 ldr r3, [pc, apache#32] @ 40 <__gcov_fork+0x40> 1c: e5932000 ldr r2, [r3] 20: e59d3004 ldr r3, [sp, apache#4] 24: e0332002 eors r2, r3, r2 28: e3a03000 mov r3, #0 2c: 1a00000 bne 3c <__gcov_fork+0x3c>" r3 is obtained by taking the value of sp offset. But after opening thumb, the second comparison value in "8c6: 4a06 ldr r2, [pc, apache#24] @ (8e0 <__gcov_fork+0x30>) 8c8: 6811 ldr r1, [r2, #0] 8ca: 687a ldr r2, [r7, apache#4] 8cc: 4051 eors r1, r2" is obtained through r7. Since r7 stores the stack address at this time, which stores the address of the parent process, the stack out of bounds will occur in the child process Signed-off-by: wangmingrong1 <wangmingrong1@xiaomi.com>
When enable CONFIG_STACK_CANARIES, in general, the stack check in the __gcov_fork function is: " return fork(); 18: e59f3020 ldr r3, [pc, #32] @ 40 <__gcov_fork+0x40> 1c: e5932000 ldr r2, [r3] 20: e59d3004 ldr r3, [sp, #4] 24: e0332002 eors r2, r3, r2 28: e3a03000 mov r3, #0 2c: 1a00000 bne 3c <__gcov_fork+0x3c>" r3 is obtained by taking the value of sp offset. But after opening thumb, the second comparison value in "8c6: 4a06 ldr r2, [pc, #24] @ (8e0 <__gcov_fork+0x30>) 8c8: 6811 ldr r1, [r2, #0] 8ca: 687a ldr r2, [r7, #4] 8cc: 4051 eors r1, r2" is obtained through r7. Since r7 stores the stack address at this time, which stores the address of the parent process, the stack out of bounds will occur in the child process Signed-off-by: wangmingrong1 <wangmingrong1@xiaomi.com>
When enable CONFIG_STACK_CANARIES, in general, the stack check in the __gcov_fork function is: " return fork(); 18: e59f3020 ldr r3, [pc, apache#32] @ 40 <__gcov_fork+0x40> 1c: e5932000 ldr r2, [r3] 20: e59d3004 ldr r3, [sp, #4] 24: e0332002 eors r2, r3, r2 28: e3a03000 mov r3, #0 2c: 1a00000 bne 3c <__gcov_fork+0x3c>" r3 is obtained by taking the value of sp offset. But after opening thumb, the second comparison value in "8c6: 4a06 ldr r2, [pc, apache#24] @ (8e0 <__gcov_fork+0x30>) 8c8: 6811 ldr r1, [r2, #0] 8ca: 687a ldr r2, [r7, #4] 8cc: 4051 eors r1, r2" is obtained through r7. Since r7 stores the stack address at this time, which stores the address of the parent process, the stack out of bounds will occur in the child process Signed-off-by: wangmingrong1 <wangmingrong1@xiaomi.com>
The memory should be unpoisoned for usage and poison after no use. Test: cmake -Bbuild -GNinja -DBOARD_CONFIG=mps3-an547:nsh ninja -C build qemu-system-arm -M mps3-an547 -m 2G -nographic -kernel build/nuttx Before the fix: apache#6 0x0000b95e in _assert (filename=0x47d3c "/arch/arm/src/armv8-m/arm_busfault.c", linenum=115, msg=0x47d34 "panic", regs=0x1006b14) at /home/neo/projects/nuttx/nuttx/sched/misc/assert.c:910 apache#7 0x00001000 in arm_busfault (irq=3, context=0x1006b14, arg=0x0 <up_ndelay>) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_busfault.c:115 apache#8 0x0000167a in arm_hardfault (irq=3, context=0x1006b14, arg=0x0 <up_ndelay>) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_hardfault.c:97 apache#9 0x0000af74 in irq_dispatch (irq=3, context=0x1006b14) at /home/neo/projects/nuttx/nuttx/sched/irq/irq_dispatch.c:144 apache#10 0x000004b2 in arm_doirq (irq=3, regs=0x1006b14) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_doirq.c:111 apache#11 0x000003a6 in exception_common () at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_exception.S:218 apache#12 0x00009568 in kasan_show_memory (addr=0x60000000 "", size=1, dumpsize=80) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:161 apache#13 0x0000961e in kasan_report (addr=0x60000000, size=1, is_write=false, return_address=0x40d1d <memcmp+28>) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:180 apache#14 0x00009818 in kasan_check_report (addr=0x60000000, size=1, is_write=false, return_address=0x40d1d <memcmp+28>) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:246 apache#15 0x000098a2 in __asan_load1_noabort (addr=0x60000000) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:403 apache#16 0x00040d1c in memcmp (s1=0x60000000, s2=0x53204, n=7) at /home/neo/projects/nuttx/nuttx/libs/libc/string/lib_memcmp.c:47 apache#17 0x0003862a in romfs_fsconfigure (rm=0x1007038, data=0x0 <__asan_store16>) at /home/neo/projects/nuttx/nuttx/fs/romfs/fs_romfsutil.c:976 apache#18 0x000378c0 in romfs_bind (blkdriver=0x1007008, data=0x0 <__asan_store16>, handle=0x1006e58) at /home/neo/projects/nuttx/nuttx/fs/romfs/fs_romfs.c:1192 apache#19 0x00032388 in nx_mount (source=0x53da4 "/dev/ram1", target=0x53d9c "/pic", filesystemtype=0x53d94 "romfs", mountflags=1, data=0x0 <__asan_store16>) at /home/neo/projects/nuttx/nuttx/fs/mount/fs_mount.c:432 apache#20 0x00046b1a in mps3_bringup () at /home/neo/projects/nuttx/nuttx/boards/arm/mps/mps3-an547/src/mps3_bringup.c:90 apache#21 0x00046b6e in board_app_initialize (arg=0) at /home/neo/projects/nuttx/nuttx/boards/arm/mps/mps3-an547/src/mps3_bringup.c:236 apache#22 0x00046a00 in boardctl (cmd=65281, arg=0) at /home/neo/projects/nuttx/nuttx/boards/boardctl.c:370 apache#23 0x0001d0d8 in nsh_initialize () at /home/neo/projects/nuttx/apps/nshlib/nsh_init.c:149 apache#24 0x00016e3e in nsh_main (argc=1, argv=0x1005f48) at /home/neo/projects/nuttx/apps/system/nsh/nsh_main.c:71 apache#25 0x0001a6fc in nxtask_startup (entrypt=0x16e11 <nsh_main>, argc=1, argv=0x1005f48) at /home/neo/projects/nuttx/nuttx/libs/libc/sched/task_startup.c:72 apache#26 0x000137de in nxtask_start () at /home/neo/projects/nuttx/nuttx/sched/task/task_start.c:116 apache#27 0x00000000 in ?? () kasan_report: kasan detected a read access error, address at 0x60000000,size is 1, return address: 0x40d1d kasan_show_memory: Shadow bytes around the buggy address: arm_hardfault: Hard Fault escalation: arm_busfault: PANIC!!! Bus Fault: arm_busfault: IRQ: 3 regs: 0x1006b14 arm_busfault: BASEPRI: 00000080 PRIMASK: 00000000 IPSR: 00000003 CONTROL: 00000000 arm_busfault: CFSR: 00008200 HFSR: 40000000 DFSR: 00000000 BFAR: 5fffffb0 AFSR: 00000000 arm_busfault: Bus Fault Reason: arm_busfault: Precise data bus error dump_assert_info: Current Version: NuttX 12.8.0 381d3fe Feb 12 2025 09:16:55 arm dump_assert_info: Assertion failed panic: at file: /arch/arm/src/armv8-m/arm_busfault.c:115 task: nsh_main process: nsh_main 0x16e11 After: No crash. Change-Id: I743783025aa2e8b77a8439d0e8601ab24bc3e109 Signed-off-by: xuxingliang <xuxingliang@xiaomi.com>
The memory should be unpoisoned for usage and poison after no use. Test: cmake -Bbuild -GNinja -DBOARD_CONFIG=mps3-an547:nsh ninja -C build qemu-system-arm -M mps3-an547 -m 2G -nographic -kernel build/nuttx Before the fix: apache#6 0x0000b95e in _assert (filename=0x47d3c "/arch/arm/src/armv8-m/arm_busfault.c", linenum=115, msg=0x47d34 "panic", regs=0x1006b14) at /home/neo/projects/nuttx/nuttx/sched/misc/assert.c:910 apache#7 0x00001000 in arm_busfault (irq=3, context=0x1006b14, arg=0x0 <up_ndelay>) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_busfault.c:115 apache#8 0x0000167a in arm_hardfault (irq=3, context=0x1006b14, arg=0x0 <up_ndelay>) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_hardfault.c:97 apache#9 0x0000af74 in irq_dispatch (irq=3, context=0x1006b14) at /home/neo/projects/nuttx/nuttx/sched/irq/irq_dispatch.c:144 apache#10 0x000004b2 in arm_doirq (irq=3, regs=0x1006b14) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_doirq.c:111 apache#11 0x000003a6 in exception_common () at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_exception.S:218 apache#12 0x00009568 in kasan_show_memory (addr=0x60000000 "", size=1, dumpsize=80) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:161 apache#13 0x0000961e in kasan_report (addr=0x60000000, size=1, is_write=false, return_address=0x40d1d <memcmp+28>) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:180 apache#14 0x00009818 in kasan_check_report (addr=0x60000000, size=1, is_write=false, return_address=0x40d1d <memcmp+28>) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:246 apache#15 0x000098a2 in __asan_load1_noabort (addr=0x60000000) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:403 apache#16 0x00040d1c in memcmp (s1=0x60000000, s2=0x53204, n=7) at /home/neo/projects/nuttx/nuttx/libs/libc/string/lib_memcmp.c:47 apache#17 0x0003862a in romfs_fsconfigure (rm=0x1007038, data=0x0 <__asan_store16>) at /home/neo/projects/nuttx/nuttx/fs/romfs/fs_romfsutil.c:976 apache#18 0x000378c0 in romfs_bind (blkdriver=0x1007008, data=0x0 <__asan_store16>, handle=0x1006e58) at /home/neo/projects/nuttx/nuttx/fs/romfs/fs_romfs.c:1192 apache#19 0x00032388 in nx_mount (source=0x53da4 "/dev/ram1", target=0x53d9c "/pic", filesystemtype=0x53d94 "romfs", mountflags=1, data=0x0 <__asan_store16>) at /home/neo/projects/nuttx/nuttx/fs/mount/fs_mount.c:432 apache#20 0x00046b1a in mps3_bringup () at /home/neo/projects/nuttx/nuttx/boards/arm/mps/mps3-an547/src/mps3_bringup.c:90 apache#21 0x00046b6e in board_app_initialize (arg=0) at /home/neo/projects/nuttx/nuttx/boards/arm/mps/mps3-an547/src/mps3_bringup.c:236 apache#22 0x00046a00 in boardctl (cmd=65281, arg=0) at /home/neo/projects/nuttx/nuttx/boards/boardctl.c:370 apache#23 0x0001d0d8 in nsh_initialize () at /home/neo/projects/nuttx/apps/nshlib/nsh_init.c:149 apache#24 0x00016e3e in nsh_main (argc=1, argv=0x1005f48) at /home/neo/projects/nuttx/apps/system/nsh/nsh_main.c:71 apache#25 0x0001a6fc in nxtask_startup (entrypt=0x16e11 <nsh_main>, argc=1, argv=0x1005f48) at /home/neo/projects/nuttx/nuttx/libs/libc/sched/task_startup.c:72 apache#26 0x000137de in nxtask_start () at /home/neo/projects/nuttx/nuttx/sched/task/task_start.c:116 apache#27 0x00000000 in ?? () kasan_report: kasan detected a read access error, address at 0x60000000,size is 1, return address: 0x40d1d kasan_show_memory: Shadow bytes around the buggy address: arm_hardfault: Hard Fault escalation: arm_busfault: PANIC!!! Bus Fault: arm_busfault: IRQ: 3 regs: 0x1006b14 arm_busfault: BASEPRI: 00000080 PRIMASK: 00000000 IPSR: 00000003 CONTROL: 00000000 arm_busfault: CFSR: 00008200 HFSR: 40000000 DFSR: 00000000 BFAR: 5fffffb0 AFSR: 00000000 arm_busfault: Bus Fault Reason: arm_busfault: Precise data bus error dump_assert_info: Current Version: NuttX 12.8.0 381d3fe Feb 12 2025 09:16:55 arm dump_assert_info: Assertion failed panic: at file: /arch/arm/src/armv8-m/arm_busfault.c:115 task: nsh_main process: nsh_main 0x16e11 After: No crash. Change-Id: I743783025aa2e8b77a8439d0e8601ab24bc3e109 Signed-off-by: xuxingliang <xuxingliang@xiaomi.com>
The memory should be unpoisoned for usage and poison after no use. Test: cmake -Bbuild -GNinja -DBOARD_CONFIG=mps3-an547:nsh ninja -C build qemu-system-arm -M mps3-an547 -m 2G -nographic -kernel build/nuttx Before the fix: apache#6 0x0000b95e in _assert (filename=0x47d3c "/arch/arm/src/armv8-m/arm_busfault.c", linenum=115, msg=0x47d34 "panic", regs=0x1006b14) at /home/neo/projects/nuttx/nuttx/sched/misc/assert.c:910 apache#7 0x00001000 in arm_busfault (irq=3, context=0x1006b14, arg=0x0 <up_ndelay>) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_busfault.c:115 apache#8 0x0000167a in arm_hardfault (irq=3, context=0x1006b14, arg=0x0 <up_ndelay>) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_hardfault.c:97 apache#9 0x0000af74 in irq_dispatch (irq=3, context=0x1006b14) at /home/neo/projects/nuttx/nuttx/sched/irq/irq_dispatch.c:144 apache#10 0x000004b2 in arm_doirq (irq=3, regs=0x1006b14) at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_doirq.c:111 apache#11 0x000003a6 in exception_common () at /home/neo/projects/nuttx/nuttx/arch/arm/src/armv8-m/arm_exception.S:218 apache#12 0x00009568 in kasan_show_memory (addr=0x60000000 "", size=1, dumpsize=80) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:161 apache#13 0x0000961e in kasan_report (addr=0x60000000, size=1, is_write=false, return_address=0x40d1d <memcmp+28>) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:180 apache#14 0x00009818 in kasan_check_report (addr=0x60000000, size=1, is_write=false, return_address=0x40d1d <memcmp+28>) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:246 apache#15 0x000098a2 in __asan_load1_noabort (addr=0x60000000) at /home/neo/projects/nuttx/nuttx/mm/kasan/hook.c:403 apache#16 0x00040d1c in memcmp (s1=0x60000000, s2=0x53204, n=7) at /home/neo/projects/nuttx/nuttx/libs/libc/string/lib_memcmp.c:47 apache#17 0x0003862a in romfs_fsconfigure (rm=0x1007038, data=0x0 <__asan_store16>) at /home/neo/projects/nuttx/nuttx/fs/romfs/fs_romfsutil.c:976 apache#18 0x000378c0 in romfs_bind (blkdriver=0x1007008, data=0x0 <__asan_store16>, handle=0x1006e58) at /home/neo/projects/nuttx/nuttx/fs/romfs/fs_romfs.c:1192 apache#19 0x00032388 in nx_mount (source=0x53da4 "/dev/ram1", target=0x53d9c "/pic", filesystemtype=0x53d94 "romfs", mountflags=1, data=0x0 <__asan_store16>) at /home/neo/projects/nuttx/nuttx/fs/mount/fs_mount.c:432 apache#20 0x00046b1a in mps3_bringup () at /home/neo/projects/nuttx/nuttx/boards/arm/mps/mps3-an547/src/mps3_bringup.c:90 apache#21 0x00046b6e in board_app_initialize (arg=0) at /home/neo/projects/nuttx/nuttx/boards/arm/mps/mps3-an547/src/mps3_bringup.c:236 apache#22 0x00046a00 in boardctl (cmd=65281, arg=0) at /home/neo/projects/nuttx/nuttx/boards/boardctl.c:370 apache#23 0x0001d0d8 in nsh_initialize () at /home/neo/projects/nuttx/apps/nshlib/nsh_init.c:149 apache#24 0x00016e3e in nsh_main (argc=1, argv=0x1005f48) at /home/neo/projects/nuttx/apps/system/nsh/nsh_main.c:71 apache#25 0x0001a6fc in nxtask_startup (entrypt=0x16e11 <nsh_main>, argc=1, argv=0x1005f48) at /home/neo/projects/nuttx/nuttx/libs/libc/sched/task_startup.c:72 apache#26 0x000137de in nxtask_start () at /home/neo/projects/nuttx/nuttx/sched/task/task_start.c:116 apache#27 0x00000000 in ?? () kasan_report: kasan detected a read access error, address at 0x60000000,size is 1, return address: 0x40d1d kasan_show_memory: Shadow bytes around the buggy address: arm_hardfault: Hard Fault escalation: arm_busfault: PANIC!!! Bus Fault: arm_busfault: IRQ: 3 regs: 0x1006b14 arm_busfault: BASEPRI: 00000080 PRIMASK: 00000000 IPSR: 00000003 CONTROL: 00000000 arm_busfault: CFSR: 00008200 HFSR: 40000000 DFSR: 00000000 BFAR: 5fffffb0 AFSR: 00000000 arm_busfault: Bus Fault Reason: arm_busfault: Precise data bus error dump_assert_info: Current Version: NuttX 12.8.0 381d3fe Feb 12 2025 09:16:55 arm dump_assert_info: Assertion failed panic: at file: /arch/arm/src/armv8-m/arm_busfault.c:115 task: nsh_main process: nsh_main 0x16e11 After: No crash. Signed-off-by: xuxingliang <xuxingliang@xiaomi.com>
No description provided.