ju/ednx/JD-1: Microsite aware key-secret pairs for oauth#433
ju/ednx/JD-1: Microsite aware key-secret pairs for oauth#433mariajgrimaldi merged 1 commit intoednx/juniper+edunextfrom
Conversation
84aa091 to
e86c68a
Compare
 felipemontoya
left a comment
felipemontoya
left a comment
There was a problem hiding this comment.
I would like to understand the consequences of the key change as well as the data changes that we would need to do in the PROD data for this to work with the current clients
a9ab879 to
62e7b1c
Compare
c875fd2 to
a00736f
Compare
| "ENABLE_THIRD_PARTY_AUTH", | ||
| settings.FEATURES.get("ENABLE_THIRD_PARTY_AUTH") | ||
| # This forces the module to be enabled on a per tenant basis | ||
| settings.FEATURES.get("ENABLE_THIRD_PARTY_AUTH_FOR_TEST", False) |
There was a problem hiding this comment.
why is this necessary, there is a consequence if this returns None instead of False ?
There was a problem hiding this comment.
I cherry-picked this from ir/ednx/JD-1. I'm gonna do some tests to check if there's a consequence
There was a problem hiding this comment.
do you know why is this change? I can't figure it out. @felipemontoya
There was a problem hiding this comment.
I remember something about this needing to be turned on when the server starts (aka the yml file) and then be turned off for all the tenants which dont have a need for it.
3088c65 to
c42442b
Compare
0e185ce to
642cf20
Compare
|
do you agree to merge this? @felipemontoya |
642cf20 to
1073c55
Compare
 felipemontoya
left a comment
felipemontoya
left a comment
There was a problem hiding this comment.
Maybe I missed something or we already tried and something was not working, but in this particular point I think we should consider again modifying the .current method.
| "ENABLE_THIRD_PARTY_AUTH", | ||
| settings.FEATURES.get("ENABLE_THIRD_PARTY_AUTH") | ||
| # This forces the module to be enabled on a per tenant basis | ||
| settings.FEATURES.get("ENABLE_THIRD_PARTY_AUTH_FOR_TEST", False) |
There was a problem hiding this comment.
I remember something about this needing to be turned on when the server starts (aka the yml file) and then be turned off for all the tenants which dont have a need for it.
8f9377b to
132411a
Compare
- Change KEY_FIELD from KEY_FIELDS = ('backend_name') to KEY_FIELDS = ('site_id', 'backend_name')
- Override provider_id to cast field
- Override current method to pass site_id
132411a to
b86108e
Compare
Description
This PR allows each tenant to have its own key-secret pair.
Changes and justification
KEY_FIELDS = ('backend_name')toKEY_FIELDS = ('site_id', 'backend_name',): this allows to create differents OauthProviderConfig per site.For example:
With
KEY_FIELDS = ('backend_name'), we could only have a max of active OauthProviderConfig equals the number of available backends.Say that we have an active OauthProviderConfig for Google and Facebook, if we add a new one for Google even with different data but with the same backend -for Google-, the old config will be updated and the new one will be the active.
Here some proof of that:
I had a Provider Configuration with the backend: google-oauth2 for the site .ngrok.io
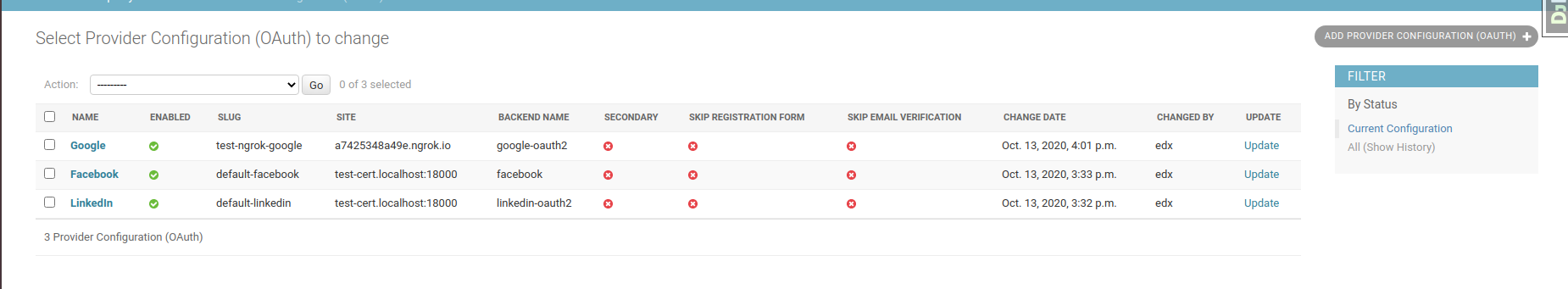
After I added a new Config for test-cert with the same backend, this happened:
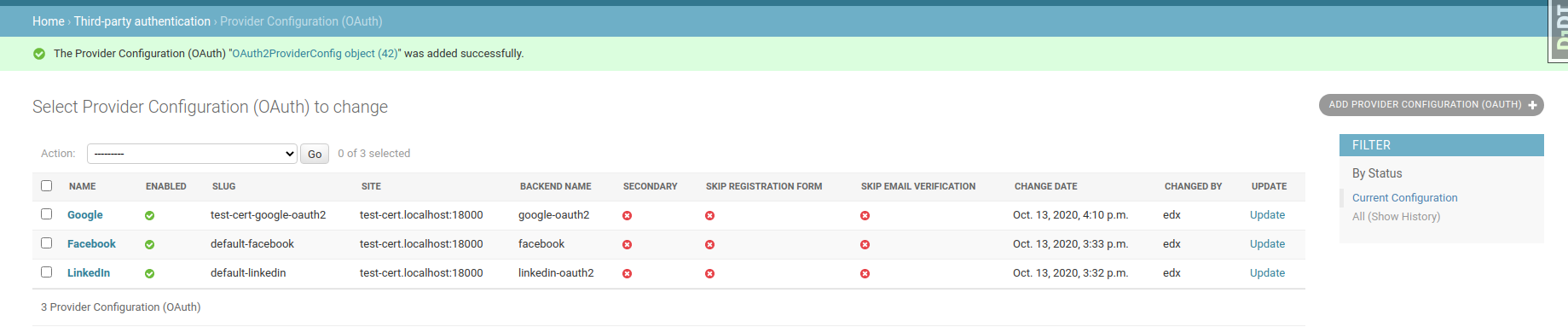
But with
KEY_FIELDS = ('site_id', 'backend_name')we can have the same max but per site, so we can have for each site a new config but with different backends.For this, I followed this PR: /edx/edx-platform/pull/17276
Pass site_id to current method calls: after changing KEY_FIELDS the current will use them as lookup fields to find the current configs, so now we have to pass the site_id.
Override provider_id to cast field: adding site_id to KEY_FIELDS makes
provider_idto change and add site_id (which is a number).Change get_setting so the key can be searched in settings: this makes it more flexible to store key/secrets, they can be stored using the OauthProviderConfig or the tenant settings.
Consequences
Data changes
https://docs.google.com/document/d/1CMoG_YoaYIuIGLQG2kDbvMQ4k0QNpu4GXAd3bSplCxA
Questions and possible answers
Here
edunext-platform/common/djangoapps/third_party_auth/provider.py
Line 34 in 9a69118
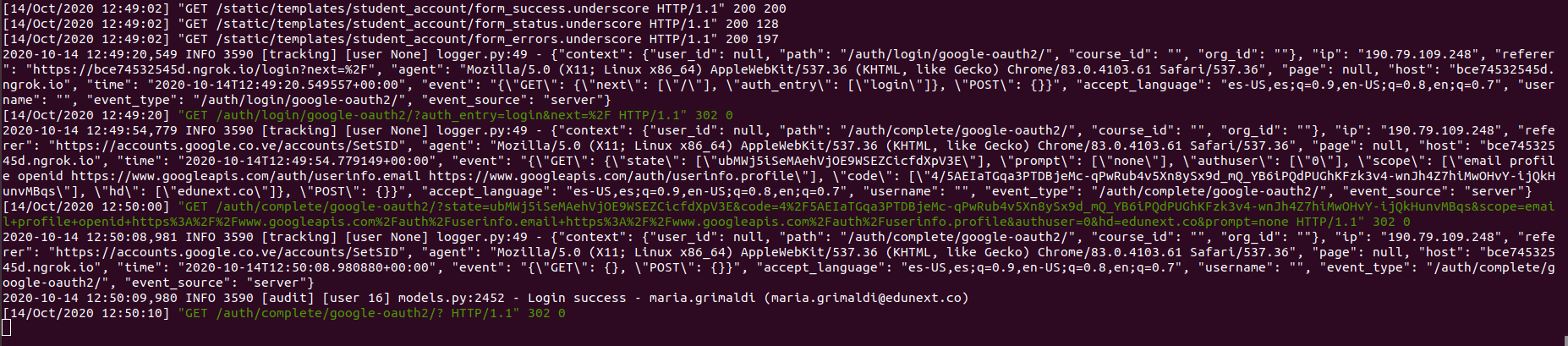
LMS logs during the login process using Google: